Surely you have already heard about the vulnerabilities in current processors in the current press last week. The critical thing about this gap is the fact that it is a security gap in the hardware and thus no logging exists. Specifically, the methods described in Meltdown and Spectre fail to delimit memory areas between different applications. Thus, it is possible to access other data that is currently available in the processor's memory.
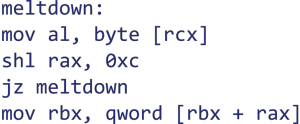
More information about the background of Meltdown and Spectre can also be found on the official website of Graz University of Technology: https://meltdownattack.com
Updates for customer systems
We recommend that all customers install updates on their own server as soon as they are available. Please check the web pages of your operating system or Linux distribution. If you have any questions about this or would like to contact our Support need, we are of course at your disposal gladly available.
For all ScaleUp server customers that have operating system updates as an option, we will install updates to your servers as they become available.
Left:
Windows Server: https://support.microsoft.com/en-us/help/4072698/windows-server-guidance-to-protect-against-the-speculative-execution
RedHat Linux: https://access.redhat.com/security/vulnerabilities/speculativeexecution
Debian Linux: https://security-tracker.debian.org/tracker/CVE-2017-5754
Ubuntu Linux: https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SpectreAndMeltdown
CloudLinux: https://www.cloudlinux.com/cloudlinux-os-blog/entry/intel-cpu-bug-kernelcare-and-cloudlinux


